Top Blockchain Architect Interview Questions
While preparing for a Blockchain Architect interview, you should focus on key technical facets that companies prioritize when evaluating candidates. We have created a list of essential questions that cover crucial topics like blockchain fundamentals, architectural design, security, and smart contracts. Mastering this knowledge will give you the confidence to navigate technical challenges during the interview and showcase your ability to design scalable, secure blockchain solutions.
Blockchain Fundamentals
This section focuses on the fundamental concepts of blockchain technology that are crucial for understanding any blockchain-based solution. These questions assess your grasp of the essential principles for a Blockchain Architect role, such as consensus mechanisms and cryptographic methods.
1. What Is the Difference Between Hyperledger and Blockchain?
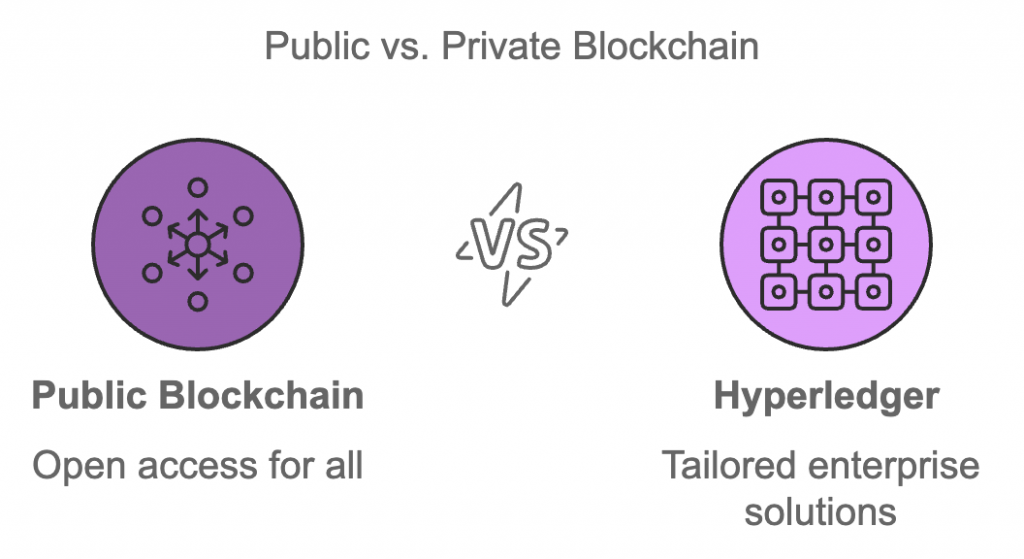
Blockchain is a decentralized technology designed to store immutable records of transactions. It applies across various industries, including finance, healthcare, and supply chain management. In contrast, Hyperledger is a platform for enterprises to develop private, permissioned blockchain solutions. Unlike public blockchains, Hyperledger focuses on improving efficiency and confidentiality, primarily for business use.
The key difference lies in their applications: while public blockchains, like Bitcoin, are open and accessible to everyone, Hyperledger is specifically designed for enterprise environments where privacy and control are crucial. Hyperledger allows developers to create tailored blockchain applications without cryptocurrency or mining, which is common in public blockchains.
2. What Is a Merkle Tree in Blockchain?
A Merkle Tree is a critical data structure used in blockchain systems to verify and maintain data integrity. It organizes transactions into a binary tree format, where each leaf node represents a cryptographic hash of a block of transaction data. The non-leaf nodes, in turn, hold the hash of their child nodes, forming a hierarchical structure.
The root hash, known as the Merkle Root, is the single point of reference for all the transactions in the block. This setup enables efficient verification of individual transactions’ validity without downloading or processing the entire blockchain.
3. How Does Cryptography Ensure Security in Blockchain?
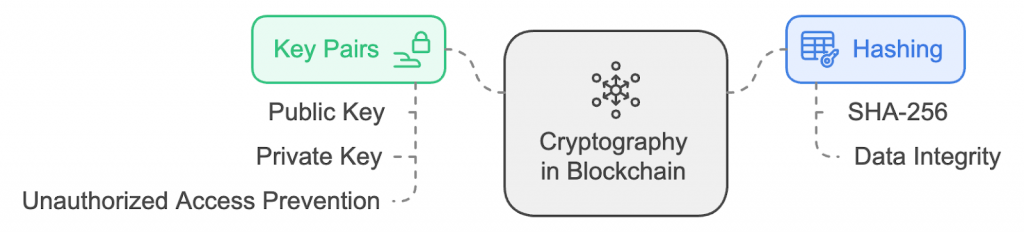
Cryptography is essential for securing blockchain networks by protecting user identities and ensuring transaction integrity. In blockchain, cryptographic hash functions, such as SHA-256, are used to encrypt data blocks. These functions convert input data into a unique, fixed-length output string called a hash. Even a small change in the input will produce an entirely different hash, making it clear when data has been tampered with.
Blockchain systems rely on public and private key pairs to secure transactions alongside hashing. The public key is shared with others to receive funds or information, while the private key is kept secret and used to sign and authorize transactions. This ensures that only the rightful owner of the private key can access and control their assets, making the system highly resilient to unauthorized access.
Blockchain Architecture
This section delves into the design and structure of blockchain systems, focusing on how scalable and secure architectures are created and integrated into existing infrastructures.
4. How Do You Approach Designing a Scalable Blockchain Architecture?
Designing scalable blockchain architectures involves analyzing the network’s specific needs, such as transaction throughput and security. One common solution is sharding, which divides the blockchain into smaller parts (shards), each of which can process transactions independently. This allows for parallel transaction processing, improving overall scalability.
Another approach is using Layer 2 solutions, such as state channels and sidechains, to offload some transactions from the main chain. These solutions enable transactions to be processed off-chain while maintaining security and integrity. Furthermore, the choice of consensus mechanisms, such as Proof of Stake, also influences scalability by reducing the need for energy-intensive computations.
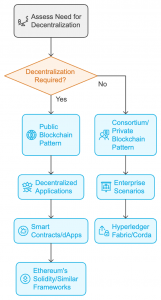
5. What Architectural Patterns and Frameworks Do You Use When Designing Blockchain Solutions?
The choice of architectural patterns depends on the specific project requirements. Since the public blockchain pattern allows open access and transparency, it is most suitable for decentralized applications. However, a consortium or private blockchain pattern is more appropriate are considered more relevant in enterprise scenarios where control and privacy are crucial. Hyperledger Fabric and Corda are well-known frameworks used in these cases to enable permissioned networks with controlled access.
For smart contracts and dApps, Ethereum’s Solidity or similar frameworks are often used to build automated, trustless systems that operate on decentralized networks.
6. How Do You Integrate Blockchain With Existing Systems?
Integrating blockchain with existing systems requires APIs or middleware to facilitate communication between the blockchain and the legacy infrastructure. The first step is mapping out data synchronization requirements to ensure consistent records between both systems. APIs can transfer data securely between the two systems while maintaining blockchain-specific elements like immutability.
Security measures such as encryption and proper access control must also be applied to safeguard the blockchain and legacy systems from vulnerabilities during integration.
Security and Privacy
Blockchain technology strongly emphasizes security and privacy, both of which are critical in ensuring the safe handling of digital assets and data. Unsurprisingly, some questions will be about this topic.
7. How Do You Ensure the Security and Integrity of a Blockchain Network?
Ensuring security in a blockchain network requires using cryptographic protocols like hash functions and secure key management systems. Hash functions, such as SHA-256, ensure that any change to a block’s data will be immediately detected, preserving the blockchain integrity. Consensus mechanisms like Proof of Stake or Proof of Work further reinforce the network by preventing malicious actors from gaining control.
Regular audits and code reviews of smart contracts and network operations are the backbone of identifying and mitigating potential vulnerabilities that could be exploited.
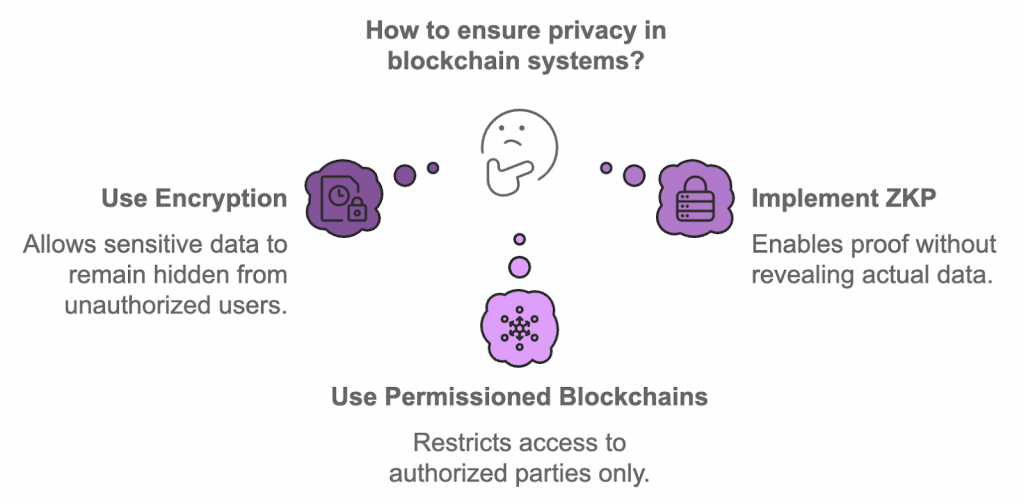
8. How Do You Maintain Data Privacy in Blockchain Architecture?
Privacy in blockchain systems is challenging due to their inherently transparent nature. However, several techniques, such as encryption, keep sensitive data hidden from unauthorized users. Zero-knowledge proofs (ZKP) are another method that enables one party to prove something to another without revealing the actual data itself.
In permissioned or private blockchain setups, access control mechanisms can ensure that only authorized parties can access specific data. These private networks balance the need for privacy while still utilizing blockchain’s immutable and decentralized aspects.
9. How Do You Secure Digital Assets and Wallets Within Blockchain Systems?
Securing digital assets involves using multi-signature wallets, which require multiple parties to authorize transactions. This minimizes the risk of unauthorized transactions by ensuring no single party can control a wallet independently. Hardware wallets and cold storage are also commonly used to keep private keys offline, protecting them from potential online threats.
Secure essential management practices and regular network monitoring are also crucial for detecting suspicious activities and maintaining the system’s integrity.
Smart Contracts and Scalability
Smart contracts and scalability are two main points of blockchain architecture. This section highlights the role of smart contracts in automating processes and explores the methods used to improve blockchain scalability.
10. What Are Smart Contracts, and How Do You Ensure Their Reliability?
Smart contracts are pieces of code that execute automatically when predefined conditions are met, making them a core element in decentralized applications and token transactions. These contracts enable trustless interactions between parties, eliminating the need for third-party intermediaries.
To ensure that smart contracts operate reliably, developers must conduct rigorous code reviews and use formal verification tools to detect potential vulnerabilities. Additionally, performing extensive unit tests and running simulations in environments like Ethereum Testnet allows developers to identify and address any flaws before launching the contract on the main blockchain.
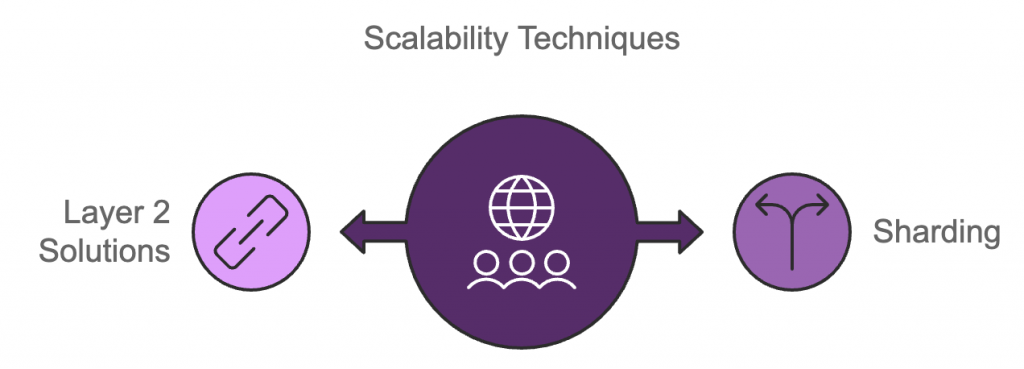
11. How Do You Address Scalability Issues in Blockchain Networks?
Scalability remains one of the most enduring obstacles for public blockchains, such as Ethereum and Bitcoin, which face challenges in efficiently processing high volumes of transactions. A widely-used technique to boost scalability is sharding. Sharding involves splitting the blockchain into smaller sections called shards, each capable of processing transactions. This reduces the workload on the entire network and allows for parallel transaction processing.
Another approach to enhancing scalability is using Layer 2 solutions, including state channels and sidechains. These techniques enable certain transactions to be processed off-chain and later settled on-chain, maintaining security while reducing the burden on the primary network.
12. How Does Sharding Improve Blockchain Scalability?
Sharding enhances scalability by dividing the blockchain into smaller, more manageable segments known as shards. Each shard is responsible for independently processing its transactions and smart contracts, enabling the system to handle countless transactions in parallel. This significantly increases throughput and efficiency.
Although shards process transactions separately, they still communicate with the main blockchain to maintain data integrity and ensure consistency across the network. This method helps address the blockchain scalability challenge by distributing the data processing load, a technique that is being adopted by platforms like Ethereum 2.0 to overcome current limitations.
Conclusion
Mastering the technical aspects of blockchain architecture is crucial for success in a Blockchain Architect interview. The key topics we’ve covered, such as blockchain fundamentals, architecture design, security, smart contracts, and scalability, represent the core competencies that interviewers will focus on. By preparing for these questions and understanding their principles, you’ll be well-equipped to demonstrate your expertise and problem-solving skills.